Best Of
Fireware v2026.1 out as of Jan 29, 2026 for 9 firewall models
FYI
For Firebox models: T115-W, T125, T145, T185, M295, M395, M495, M595, M695
Announcing the WatchGuard Idea Portal
WatchGuard community users and customers,
We've listened to your feedback about product enhancement requests and have been hard at work to provide you with a better system. The WatchGuard Idea Portal allows you to submit ideas directly to our Product Management team and receive feedback on your requests.
You can navigate to the Idea Portal by logging into WatchGuard Cloud. https://cloud.watchguard.com
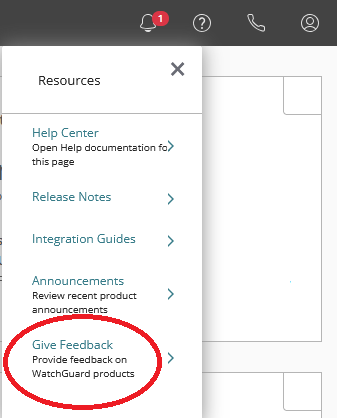
-Click the question mark at the top right of the page and select Give Feedback.
-The idea portal will load and allow you to make submissions for new ideas or upvote existing requests.
Thank you,
Announcing the WatchGuard Idea Portal
WatchGuard community users and customers,
We've listened to your feedback about product enhancement requests and have been hard at work to provide you with a better system. The WatchGuard Idea Portal allows you to submit ideas directly to our Product Management team and receive feedback on your requests.
You can navigate to the Idea Portal by logging into WatchGuard Cloud. https://cloud.watchguard.com
-Click the question mark at the top right of the page and select Give Feedback.
-The idea portal will load and allow you to make submissions for new ideas or upvote existing requests.

Thank you,
Announcing the WatchGuard Idea Portal
WatchGuard community users and customers,
We've listened to your feedback about product enhancement requests and have been hard at work to provide you with a better system. The WatchGuard Idea Portal allows you to submit ideas directly to our Product Management team and receive feedback on your requests.
You can navigate to the Idea Portal by logging into WatchGuard Cloud. https://cloud.watchguard.com
-Click the question mark at the top right of the page and select Give Feedback.
-The idea portal will load and allow you to make submissions for new ideas or upvote existing requests.

Thank you,
New way to submit product enhancement requests.
WatchGuard community users and customers,
We've listened to your feedback about product enhancement requests and have been hard at work to provide you with a better system. The WatchGuard Idea Portal allows you to submit ideas directly to our Product Management team and receive feedback on your requests.
You can navigate to the Idea Portal by logging into WatchGuard Cloud. https://cloud.watchguard.com
-Click the question mark at the top right of the page and select Give Feedback.
-The idea portal will load and allow you to make submissions for new ideas or upvote existing requests.

Thank you,
Re: Access Portal - Reverse Proxy - OWA: Attachment size limited?
Solution:
- Login via SSH into Firebox.
- Start config-mode with configure
- no access-portal url-mappings proxy-buffering enable
I found this command in this KB article because I got the same [crit] log message. https://techsearch.watchguard.com/KB/WGKnowledgeBase?lang=en_US&SFDCID=kA10H000000g4bRSAQ&type=Known+Issues
Re: iPadOS18 IKEv2 Mobile VPN + Authpoint
Hi,
I ran into the same issue (payload ID size too small) in a slightly different setup (IKEv2, Radius, iOS18) and found that the client profile for the IKEv2 Mobile VPN does not contain a LocalID, which seems to bother iOS at least on the iPhone.
My solution/workaround/whatever you call it was:
- download the client profile from the WG Appliance
- extract, dive into the MacOS_iOS-Folder
- edit the xxx.mobileconfig with your favourite text editor
- find the <key>LocalIdentifier</key> tag, which should be followed by an empty <string /> tag
- insert an identifier into that string-tag, a UFQDN like user@vpn.internal should suffice, it seems not to be verified anywhere (though I did not run any IKE message tracing)
the segment should then look like
<key>LocalIdentifier</key>
<string>user@vpn.internal</string>save, then airdrop/push the .mobileconfig to the iOS-device and install.
worked for me.
Have a good day.
Re: Cannot login to Dimension
You can move the old Dimension database to the new instance of Dimension.
Move the Dimension Database to a new Dimension Server
https://www.watchguard.com/help/docs/help-center/en-US/Content/en-US/Fireware/dimension/database_move_d.html
Be sure to block TCP port 80 Internet access from the new Dimension Server, as indicated in the above Known Issue link

