IKEv2 - unable to access internal resources and no internet - I can ping internal IPs
I did search this forum before asking.
I can connect to IKEv2 VPN on my iPhone and Windows 10, but I have no internet when connected.
I can ping internal devices but can't actually access them (shares, RDP).
NAT and the policy are configured correctly as per WG manual.
- 192.168.0.0/16 Any-External
- 172.16.0.0/12 Any-External
- 10.0.0.0/8 Any-External
I'm using Firebox authentication. Do I need to configure RADIUS to get it working properly or am I missing something?
Whilst it says no internet on Win10 PC and on iOS I can ping the internal devices at the FIrebox end and mobile VPN devices from the Firebox.
Using 12.5.3
Thanks in advance
Best Answers
-
@Bruce_Briggs said:
Any other policy allowing this traffic??No other traffic.
@Bruce_Briggs said:
Users added to the IKEv2-Users group may have access allowed by some other policy which includes those users.You can move the IKEv2-Users group to the top of the policy list and see what shows up.
It was on top from the beginning, I forgot to mention.
The user is member of the Fire.... hang on. Do users on the list have to be ticked?
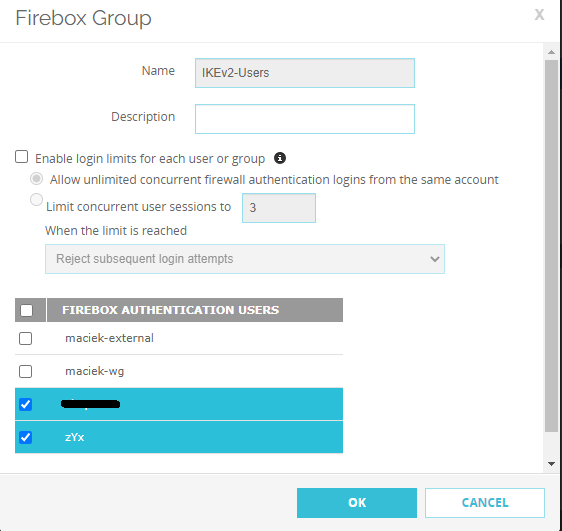
I ticked those two users, saved changes and I think it works on both, the PC and the iPhone (I'm now connected and can access the internet, remote shares and RDS).
Does it mean I added those users to the IKEv2 group? How come I managed to connect at all in the first place?
Is it me or is WG user/group management a bit confusing?

Can someone pinch me? I've been trying some time to get this working.
0 -
Looks like some other policy allowed access from your client endpoint to internal devices, for your user ID, which presumably is a member of another Firebox-DB group.
YES, you do need to make a specific user a member of an authentication group, in this case IKEv2-Users, to get the access that you desire.
PINCH.
5 -
And, even if the Allow IKEv2-Users policy was lower in the list, your HTTPS-ADFS does not include IKEv2-Users so it would not apply.
5

Answers
What do you see in Traffic Monitor when Internet access is tried?
Any denies?
You can turn on Logging on the auto created Allow IKEv2-Users policy to see packets allowed by this policy in Traffic Monitor.
Also check the DNS settings that result from the IKEv2 connection.
You can review what you have set up that IKEv2 clients should get in your XTM IKEv2 setup.
Hey Bruce,
nothing in Traffic Monitor
FYI: I can ping the mobile device from the Firebox and vice versa
Turn on Logging on the IKEv2 policy
DNSs are correct (1st is the AD DNS and 2nd is 8.8.8.8) but the gateway is set to 0.0.0.0 (in ipconfig /all)
When using VPN with SSL, the gateway is blank (in ipconfig /all) though VPN with SSL is what we are currently using with no issues.
though VPN with SSL is what we are currently using with no issues.
It is on. Nothin in Traffic Monitor.
Any other policy allowing this traffic??
Users added to the IKEv2-Users group may have access allowed by some other policy which includes those users.
You can move the IKEv2-Users group to the top of the policy list and see what shows up.
Bruce, will RADIUS config allow SSO or allow the user to use their AD credentials to authenticate? I didn't play with RADIUS yet.
Thank you BTW
SSO is only for internal users, not for VPN users.
Yes RADIUS will allow you to use AD users/groups for IKEv2 authentication.
From the docs:
https://www.watchguard.com/help/docs/help-center/en-US/Content/en-US/Fireware/mvpn/ikev2/mvpn_ikev2_about_c.html
User Authentication
Mobile VPN with IKEv2 supports local authentication on the Firebox (Firebox-DB) and RADIUS authentication servers.
If your users authenticate to network resources with Active Directory, we recommend that you configure RADIUS authentication so the IKEv2 VPN can pass through Active Directory credentials.
For more information about authentication, see About Mobile VPN with IKEv2 User Authentication.
https://www.watchguard.com/help/docs/help-center/en-US/Content/en-US/Fireware/mvpn/ikev2/mvpn_ikev2_user_auth.html
Not sure if it's user/authentication related, but when I'm connected to IKEv2 VPN and I try to log in to our O365 portals, the adfs.company.com redirects me to SSLVPN_LOGON.shtml page. I only noticed it this morning as my online session with M$ timed out since last night.
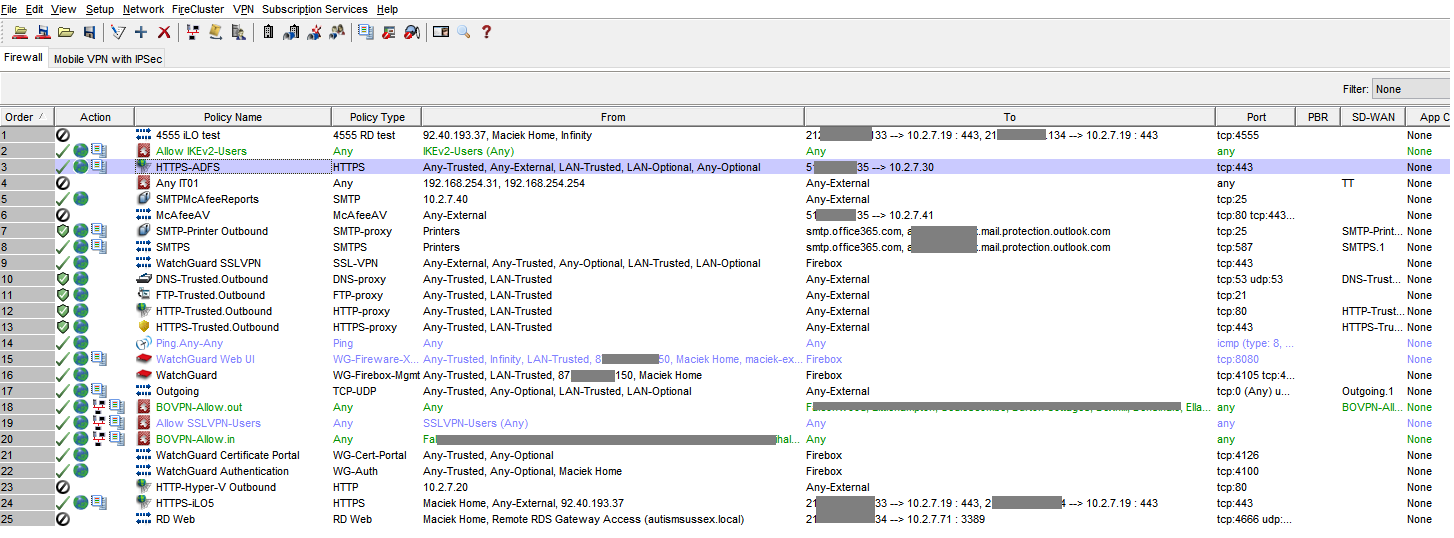
I have HTTPS-ADFS policy set on port 443 to redirect users to our internal ADFS server to authenticate when logging in to o365 apps online.
It's like the HTTPS-ADFS policy is ignored...
enlarge image
I am a bit confused as to why this is happening. Do you mind having a look for me?
Not sure if this is user/authentication related, but when logging in to o365 portals adfs.comany.com is now redirecting me to /sslvpn_logon.shtml page.
It's like HTTPS-ADFS policy is being ignored...
enlarge image
I am a bit confused as to why this is happening... would you mind having a look for me?
(all important IPs and have been hidden)
Because all traffic from IKEv2 users is using the 2nd policy, not the 3rd policy.
Bruce, I apologise for not mentioning this, but I've only just moved the IKEv2 policy above the HTTPS-ADFS policy as it was below it before. Made no difference.
I was thinking that but, HTTPS-ADFS doesn't include SSLVPN users either and those users have no issues with ADFS.
I added IKEv2 users to HTTPS-ADFS policy and it seems to have fixed it.
How is it working for SSLVPN users? SSLVPN users are authenticated with AD.
Q: How is it working for SSLVPN users?
A: no idea if SSLVPN is set up for routing. If it is set up for bridge, then the SSLVPN IP addrs would get whatever the bridge group is set up for, such as Trusted.