Mobile VPN DNS "Use Network Settings"
When setting up Mobile VPN and using the Use Network Settings option, VPN users cannot resolve Internal Hosts.
The context help in Watchguard Cloud says this:

So in the DNS section Public and Internal are set like this. (100.100 is used internally at client)

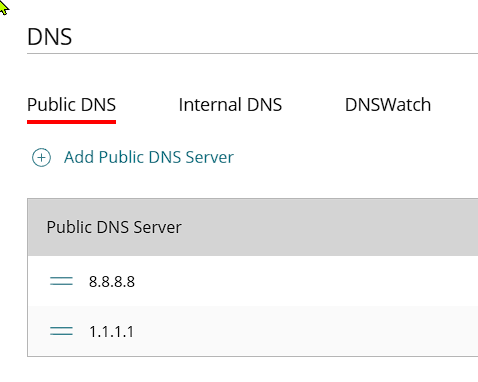
To me the above above makes sense. Any domain.com queries to by a VPN client should be answered by the servers on the Internal DNS screen. But they aren't.
The Knowledge Base gives conflicting information to Help if I am interpreting it correctly.
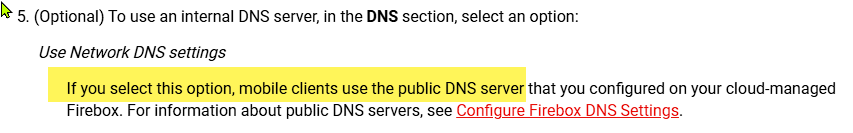
So entering an internal DNS server on the Public section is needed to resolve the Internal hosts? I works, but is this really the way it is supposed to work or is there another way to configure this that when reviewing the config does not look wrong?
Hopefully I have just overlooked something.
Comments
Here is the response from the new AI generator on the Support Center site Search function, with this search term: "and you want to assign this dns server to mobile vpn with ssl" and with Product = WatchGuard Cloud selected
===========
Assigning a DNS Server to Mobile VPN with SSL
To assign a DNS server to Mobile VPN with SSL, you have two options in the DNS section:
Use Network DNS settings: This option allows mobile clients to use the public DNS server configured on your cloud-managed Firebox. Assign Network DNS settings: Here, you can specify the domain name suffix, DNS servers, and WINS servers. For example, if you enter example.com as the domain name and 10.0.1.53 as the DNS server, mobile clients will use example.com for unqualified domain names and 10.0.1.53 as the DNS server.========
This is the way that I would expect it to work for your situation - at least it is for non-cloud Firewalls - the only kind that I have.