Block outgoing DHCP traffic to another network
Hello everyone,
we have two watchguard fireboxes connected together over a physical port. These connection uses a 10.0.10.0/24 network. Watchguard A has another network on an physical port with 192.168.160.0/23. For watchguard B its the same, instead it uses a 192.168.162.0/24 network. In each of these two networks act a DHCP Server and these two networks get routed through the 10.0.10.0/24 network. At the moment there is the problem that a DHCP discover reaches both networks and the client could get an ip address from the wrong DHCP server.
I tried to add firewall rules to block outgoing traffic for port 67 UDP and 68 UDP, but it has no effect.
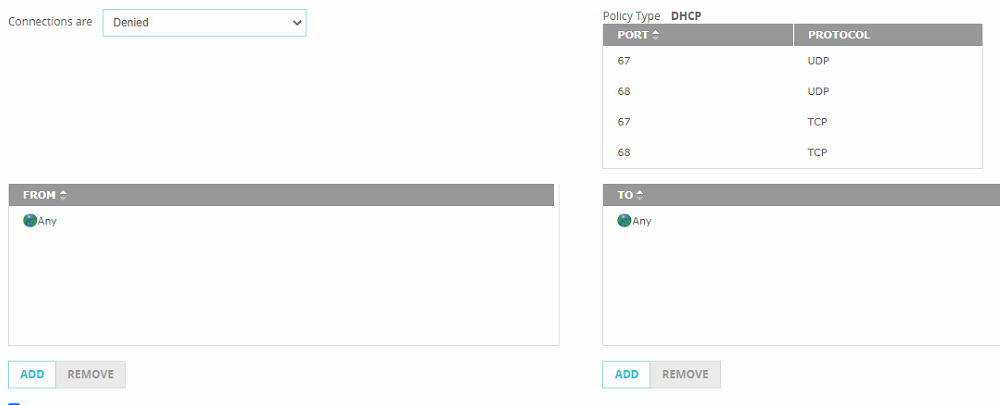
This rule is defined on both fireboxes. When I try to block for example RDP traffic, its working out of the box. Does anybody have an idea?
Thanks
Comments
The better choice is to change your network setup so that these DHCP packets don't flow where you don't want them.
Exactly what is the DHCP server? The firewalls ?
Perhaps you could interconnect the firewalls using an unused interface with a different subnet - so this problem just isn't there.
To have these policies work - block packets from the firewall itself, you need to enable the "Any from firewall" policy and then move the policies above the "Any from firewall" policy in your config.
See "Traffic Generated by the Firebox" here:
https://www.watchguard.com/help/docs/help-center/en-US/Content/en-US/Fireware/basicadmin/global_setting_define_c.html
Note that the current polices will block all DHCP packets from the firewall - so the polices will need to be modified to do exactly what you want.